Detect, Prioritize and Respond - All in One Hub
Triage Center is your command hub for AI-driven phishing remediation, enabling your team to — detect, analyze, and neutralize threats in real time before they cause damage.
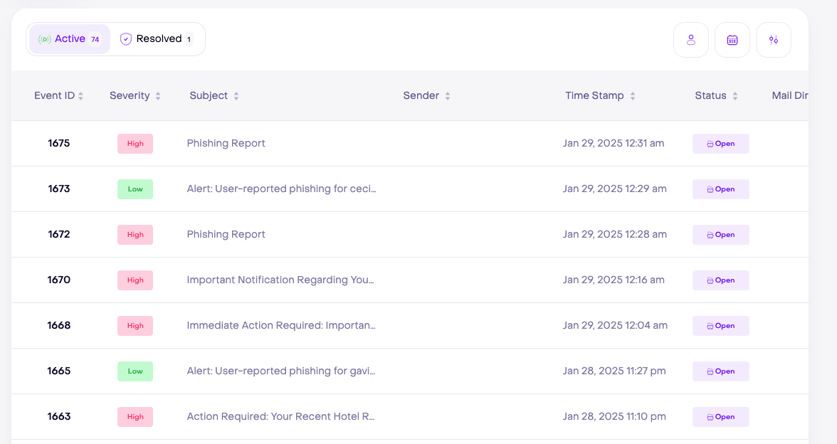
What can you expect from our
Triage function?
Instant Threat Prioritization
Jericho Security’s AI-powered email security instantly analyzes and scores incoming threats, helping security teams focus on the most dangerous phishing attempts. Our real-time threat intelligence evaluates sender reputation, content anomalies, and malicious links to prioritize high-risk emails automatically, reducing alert fatigue and improving response efficiency.
“Before Jericho, our team was drowning in phishing alerts. Now, their threat scoring pinpoints the real risks—no more sifting through noise.” – CISO, Financial Services


Automated Remediation
Stop threats before they spread with Jericho Security’s automated phishing response tools. Our system blocks malicious senders, removes phishing emails in real time, and mitigates risks with zero manual intervention. With seamless email security automation, organizations can neutralize cyber threats before employees even see them.
The ability to instantly quarantine malicious emails across our organization has been a game-changer. Jericho takes response time from hours to seconds.” – SOC Analyst, Tech Firm


Custom Training from Real Attacks
Turn live phishing threats into personalized security training with Jericho’s AI-driven simulation platform. Instead of generic phishing tests, we convert real attack data into engaging, scenario-based training for employees—strengthening awareness and reducing breach risks. Learn from actual threats, not theoretical ones.
“Jericho turns real phishing attempts into training simulations—so our employees learn from actual threats, not just generic scenarios. Our click rates on phishing tests dropped by 60% in just a few months.” – CISO, Insurance Company


Centralized Dashboard
Manage phishing threats, incident response, and user risk analytics from a single dashboard. Jericho Security’s one-click dashboard provides a centralized view of phishing cases, allowing security teams to assign, track, and remediate threats efficiently. With real-time reporting and compliance tracking, you stay ahead of evolving cyber risks.
“We used to struggle with fragmented security tools. Jericho’s centralized phishing management finally gives us a real-time view of email threats and user risk, all in one place.” – IT Security Lead, Legal Services


Why Choose Triage?
The stakes have never been higher—phishing remains the leading cause of data breaches, financial fraud, and ransomware infections. Traditional security tools react too slowly and place too much burden on overwhelmed security teams. Triage Center transforms your phishing defense by delivering AI-driven speed, automation, and intelligence to neutralize threats before they cause damage.
Manual Remediation Is No Longer The Solution
The longer a phishing email sits in an inbox, the greater the risk of compromise. Manual investigation and remediation can take hours—sometimes even days—leaving your organization vulnerable.
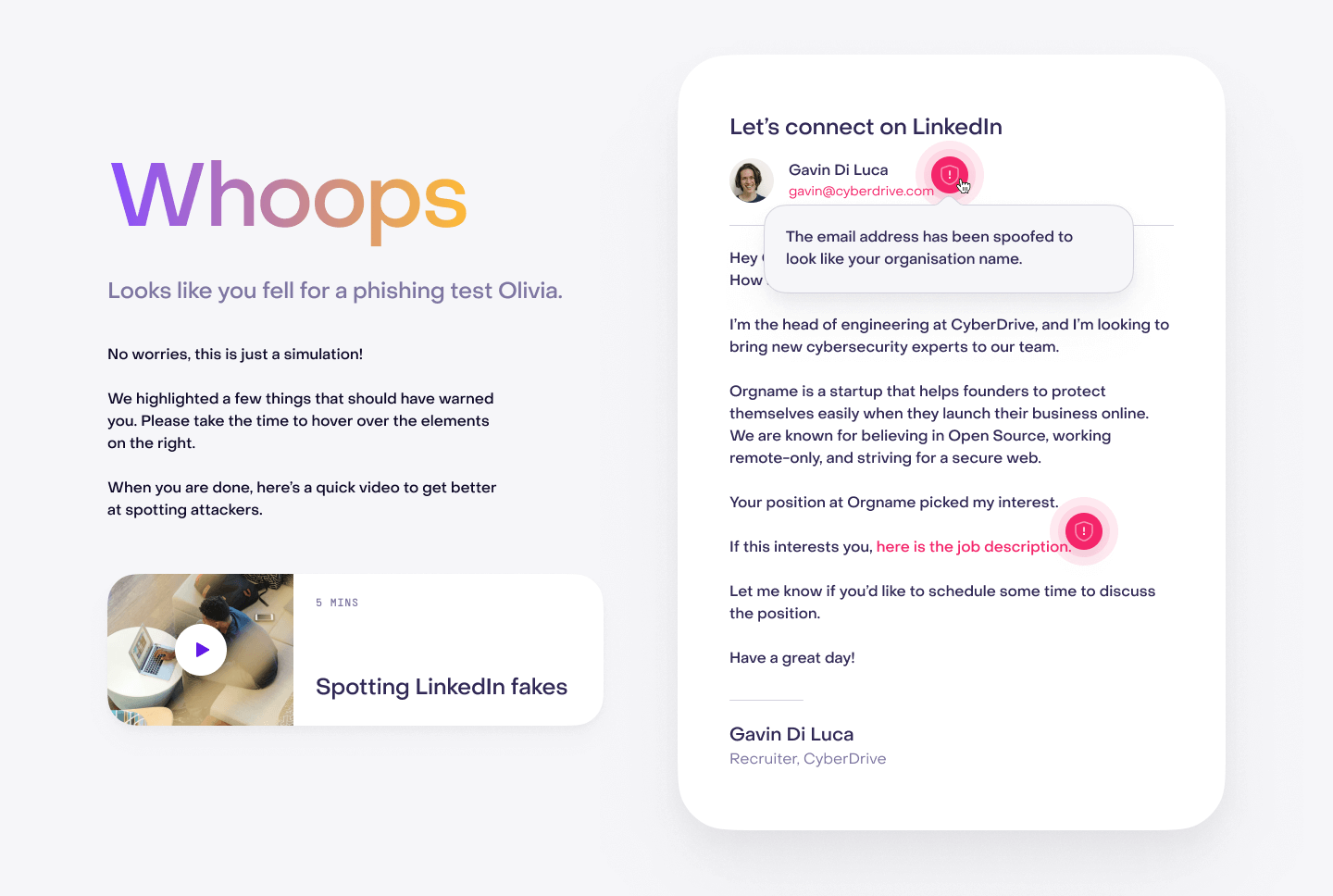
Turn Attacks into Training Opportunities
Phishing threats don’t just stop at remediation—they become learning opportunities. Jericho’s Triage Center seamlessly integrates with our Spearphishing Simulator and Training Library, allowing you to convert real phishing attempts into tailored training simulations. This adaptive learning approach ensures employees are trained on actual threats targeting your organization, increasing resilience and awareness.
Streamline Case Management
Operate from a centralized hub to track, assign, and resolve incidents efficiently. Instead of dealing with scattered alerts, security teams can manage all phishing threats from a single dashboard, reducing response times and eliminating investigation bottlenecks. With automated tracking and high-risk insights, organizations achieve faster resolutions, improved efficiency, and reduced security workload, minimizing breach risks from delayed responses.
Signs you need a Triage Solution
You struggle with investigation bottlenecks
Without a phishing triage solution, security teams spend hours manually sorting through phishing alerts, leading to delays in identifying real threats. A triage system automates threat prioritization, ensuring that high-risk emails are addressed first, reducing manual workloads, and enabling faster response times.
You’ve had a recent data breach
Every phishing attempt is a learning opportunity. A triage system not only removes threats but also converts real attacks into targeted training exercises, reinforcing security awareness and reducing future risk.
You want to scale your operations
Manually sorting through phishing alerts is inefficient and unsustainable. A triage solution automates threat analysis, response workflows, and remediation, allowing security teams to handle a higher volume of threats without additional overhead. With AI-driven insights, organizations can detect patterns, anticipate future attacks, and scale their security operations efficiently.
Phishing Triage for
proactive organizations
Jericho Security’s phishing triage solution is designed to help organizations detect, prioritize, and respond to phishing threats in real time. By analyzing incoming threats and assessing risk levels, our AI-powered triage system automates remediation, removes malicious emails before they cause harm, and ensures security teams can focus on the most pressing threats first.
Phishing Triage Solution - FAQs
What is a phishing triage solution?
A phishing triage solution is a security tool that automates the detection, prioritization, and remediation of phishing threats. It helps security teams quickly identify high-risk emails, remove threats, and manage phishing incidents efficiently, reducing the risk of compromise.
How does a triage system improve phishing response time?
By leveraging AI-driven threat scoring and automated remediation, a triage system eliminates manual investigation delays. It instantly prioritizes the most dangerous phishing emails, enabling security teams to respond in seconds instead of hours.
What happens to emails flagged as phishing?
Phishing emails are automatically quarantined, analyzed, and assigned a risk score. Security teams can then choose to block senders, remove emails from inboxes, or escalate threats for further investigation—all from a centralized dashboard.
Can a triage solution help reduce alert fatigue?
Yes, a triage system filters out low-priority and false-positive alerts, ensuring security teams only focus on the most critical threats. This reduces alert fatigue, improves efficiency, and allows analysts to dedicate time to real threats.
How does phishing triage integrate with security awareness training?
A phishing triage system can convert real-world phishing attempts into training simulations. This means employees are trained on actual threats targeting your organization, making cybersecurity awareness programs more relevant and effective.
Does a phishing triage solution work with existing email security tools?
Yes, phishing triage solutions are designed to integrate seamlessly with existing email security gateways (SEGs), SIEM platforms, and incident response tools, enhancing your organization’s overall security ecosystem.
How does a triage system support compliance efforts?
By providing detailed logs, reports, and tracking phishing response metrics, a triage solution helps organizations meet compliance requirements for data protection and cybersecurity regulations such as GDPR, HIPAA, and SOC 2.
Why is phishing triage essential for modern businesses?
With phishing being the leading cause of cyber breaches, organizations need a proactive approach to manage email threats. A phishing triage solution reduces dwell time, strengthens security defenses, and minimizes human error, keeping businesses safe from evolving cyberattacks.
Ready to get started?
It’s time to protect your business by investing in cybersecurity awareness training. At Jericho Security, our training programs are designed to educate your team, protect your data, and give you peace of mind. Protect your business from evolving cyber threats – schedule your free demo today.
Get to know the platform
Cybersecurity
Dashboard
Manage all your cybersecurity needs in one powerful, easy-to-use platform.
Customized
Training Content
Tailored training videos available on demand for more impactful results.
Performance
Analytics
Track and analyze employee performance in simulations and training.
Our industry training and solutions
At Jericho Security, we specialize in delivering innovative cybersecurity training tailored for a diverse range of industries. Our expertise extends across:
Retail
Protect customers' personal and payment information from data breaches and cyber-attacks.
Learn MoreProtect customers' personal and payment information from data breaches and cyber-attacks.
Learn MoreManufacturing
Keep your production lines and intellectual property secure with cybersecurity solutions.
Learn MoreKeep your production lines and intellectual property secure with cybersecurity solutions.
Learn MoreE-Commerce
Protect your online business from cyber threats while delivering a safer shopping experience.
Learn MoreProtect your online business from cyber threats while delivering a safer shopping experience.
Learn MoreEnergy
Safeguard critical infrastructure with targeted cybersecurity measures.
Learn MoreSafeguard critical infrastructure with targeted cybersecurity measures.
Learn MoreTechnology
Anticipate, identify, and mitigate the latest threats in the fast-paced tech industry.
Learn MoreAnticipate, identify, and mitigate the latest threats in the fast-paced tech industry.
Learn MoreFederal Government
Protect sensitive information with tools designed for the public sector.
Learn MoreProtect sensitive information with tools designed for the public sector.
Learn MoreFinancial Services
Secure your financial operations with solutions tailored to financial services.
Learn MoreSecure your financial operations with solutions tailored to financial services.
Learn MoreState & Local Government
Address the specific cybersecurity needs of state and local governments.
Learn MoreAddress the specific cybersecurity needs of state and local governments.
Learn MoreHealthcare
Keep patient data confidential and secure with compliant security solutions.
Learn MoreKeep patient data confidential and secure with compliant security solutions.
Learn MoreHigher Education
Protect the personal and academic information of your students and staff.
Learn MoreProtect the personal and academic information of your students and staff.
Learn More